*Attention* - Federating a on-premises domain with WorkspaceOne Access affects all of the domain users' authentication with Office365. It is highly recommended to perform this procedure using a test domain and test Office365 tenant first.
Federating Office 365 with Workspace One Access provides several benefits:
- Users can access their Office 365 applications directly from the Intelligent Hub catalog using Single Sign On (SSO)
- Conditional access policies can be created in Workspace One Access to validate whether a user can access their Office 365 applications or not based on device type, IP address range, whether the device is being managed by Workspace One UEM, whether the device is compromised etc..
- Besides providing single sign on capability with Browser access, with Workspace ONE UEM managing the devices mobile SSO policies can be used to provide SSO to the Office 365 native mobile apps in IOS and Android devices
- A publicly registered domain
- A Workspace One Access tenant
- A Workspace One UEM tenant
- A Windows on-premises Active Directory domain already integrated with the WorkspaceOne Access tenant
- An Office 365 subscription
- A public CA issued certificate
- Install-Module -Name AzureAD
- Install-Module -Name MSOnline
Then I used the following powershell commands to ensure the modules were installed:
- Get-Module -ListAvailable |findstr MSOnline
- Get-Module -ListAvailable |findstr AzureAD
Before proceeding with the AzureAD configuration first I downloaded, installed and executed the Microsoft IDfix tool. This tool shows any possible synchronization issue with AzureAD. It is useful to run it and remediate the synchronization issues before configuring your AzureAD federation. The IDfix tool can be downloaded using the following link: Link
At this point my lab on-premises domain was ready to be federated with my WorkspaceOne Access tenant. In order to do so I used this command on my ADFS server:
- set-MsolDomainDomainAuthentication
- set-MsolDomainAuthentication –DomainName lvalente.com –Authentication Federated –IssuerUri td-valentel.vidmpreview.com -FederationBrandName lvalenteInc -PassiveLogOnUri https://td-valentel.vidmpreview.com/SAAS/API/1.0/POST/sso -LogOffUri https://login.microsoftonline.com/logout.srf -ActiveLogOnUri https://td-valentel.vidmpreview.com/SAAS/auth/wsfed/active/logon -MetadataExchangeUri https://td-valentel.vidmpreview.com/SAAS/auth/wsfed/services/mex -SigningCertificate <WS1 Access Tenant Certificate>
Once I executed the above command successfully I used the following command to confirm my on-premises domain was now federated to my WorkspaceOne Access tenant:
- Connect-MsolService
- Get-MsolDomain
Next I had to confirm I was synching the necessary attributes required by for Office 365 SSO SAML assertion between my on-premises domain and my WorkspaceOne Access tenant. Reminding here that the pre-reqs listed at the beginning of this article included the integration between the on-premises AD domain and the WorkspaceOne Access tenant using the WorkspaceOne Access Connector was a pre-req for this exercise.
- ObjectGUID
- UserPrincipalName
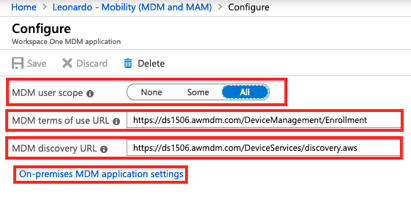
I was getting close now. The last step before testing was to set up the O365 App in WorkspaceOne Access and entitle it to my users
- the tenant attribute was mapped to my on-premises AD domain routable suffix
- that the issuer attribute was mapped to my WorkspaceOne Access tenant URL
- that in Advanced Properties the UPN attribute was mapped to the variable ${user.userPrincipalName}
- and that the ImmutableID attribute was mapped to the variable ${user.objectGUID}